Introduction
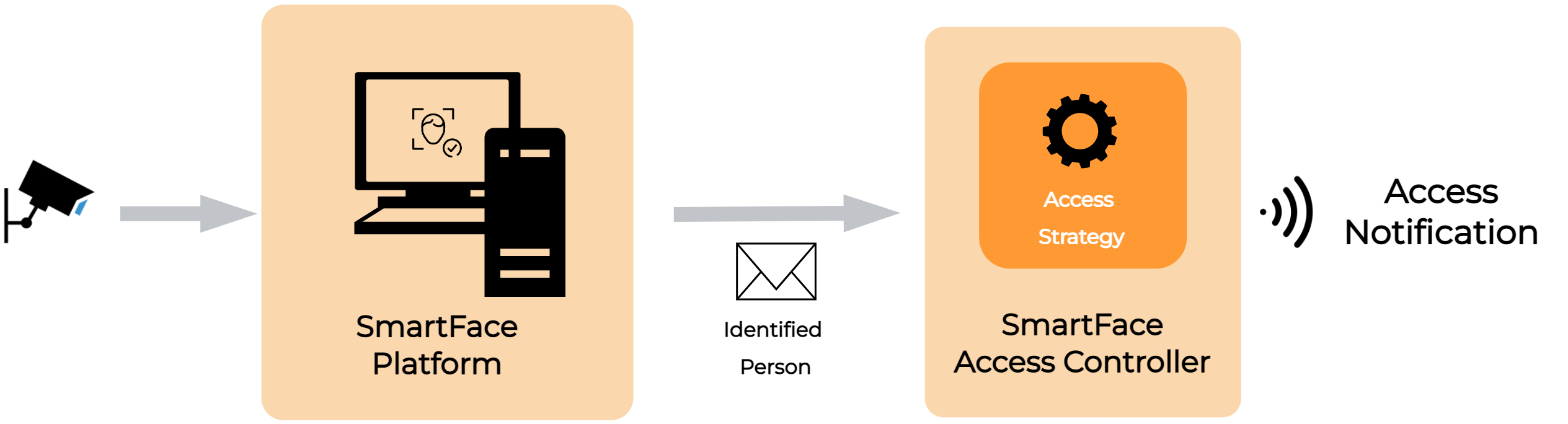
The SmartFace Access Controller is a standalone module that listens to notifications coming from the SmartFace Platform about people matched against watchlists. While the it is a standalone module, due to it’s importance it is integral part of the SmartFace Platform and is used for various solutions and use cases.
The notifications are filtered by a predefined set of rules and access control strategies. Only the notifications that pass these rules are sent out from the Access Controller. This component is used for the access control use case, where seamless and friction-less opening of access points (turnstiles, doors, barriers, ramps, etc.) is required.
Access Controller functionality
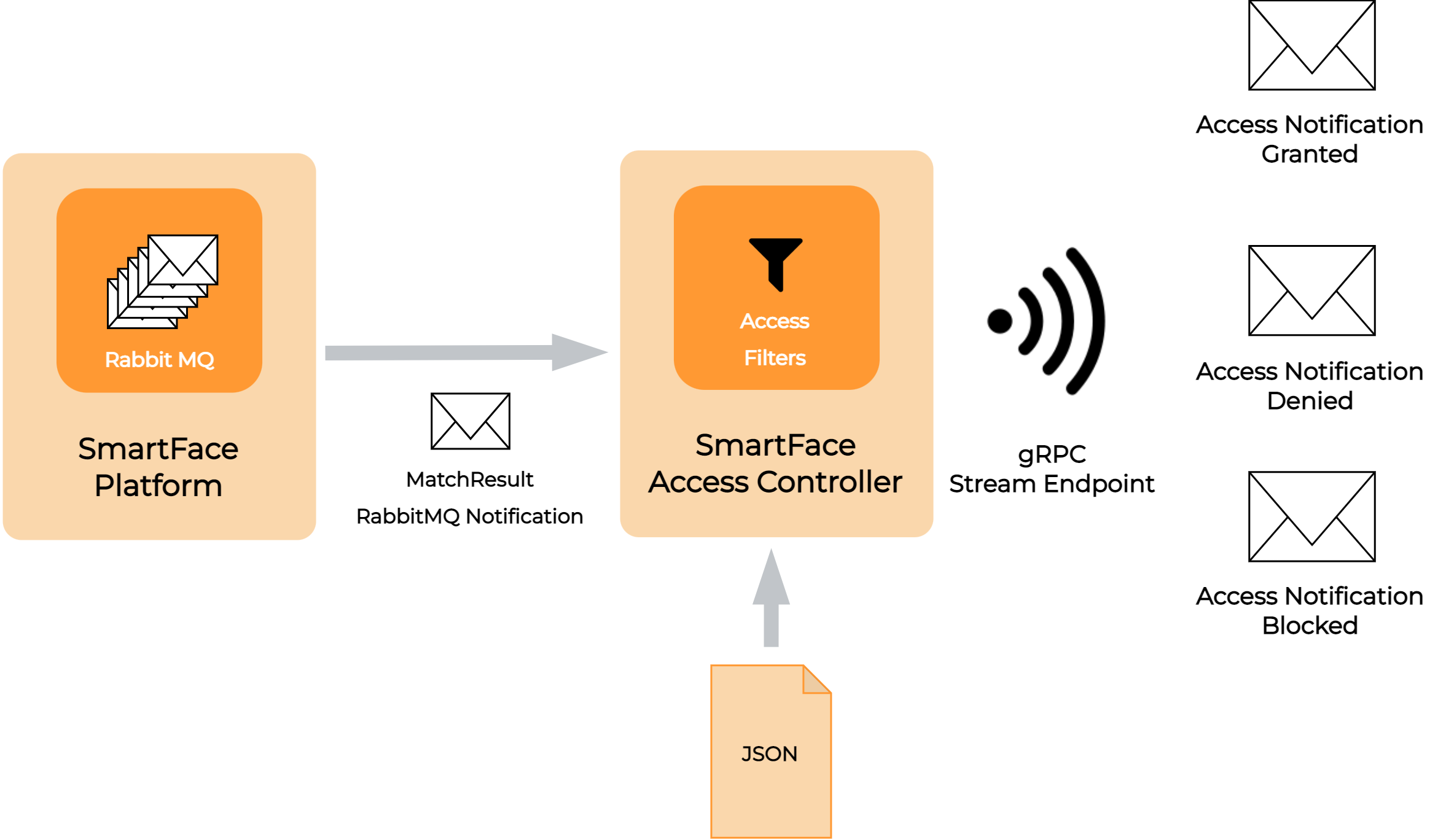
The module listens to notifications about matched persons sent by the SmartFace Platform (internal SmartFace’s RabbitMQ messages called MatchResults - available sooner than the publicly provided ZeroMQ notifications and GraphQL notifications). When a MatchResult notification passes the set of rules, it is sent out by the controller as a new access control notification. When a match notification doesn’t pass these rules, then it is thrown away. The reason behind the filtration is that SmartFace Platform notifies about all detected and identified people in the processed video/edge stream.
An identified person can stand in a background or among a group of people who aren’t registered in the watchlist. SmartFace Platform still sends notifications for all the detected people. These notifications might not be desired in the access control use case, because the authorized person can stand far from the camera or the access barrier and can be surrounded or stand behind a person that is not authorized for the access. In such a case you want the access barrier to be closed so that the unauthorized person can not enter.
The Access Controller can use predefined filtering strategies, to decide when the access should be denied, whether a notification from SmartFace Platform should be filtered out or the gRPC AccessNotification should be sent to all connected clients through the gRPC server streaming service. This behavior ensures that only authorized persons may get access through the barrier. Information about the access strategy and filters is available here.
The SmartFace Platform also supports the detection of face masks and sends notifications which contain information whether a person wears a mask. Access Controller is able to use this feature and can prevent persons who aren’t wearing a mask from passing the access barrier. This can be used to force rules related to face masks due to epidemics.
Notifications
Access Controller sends out three types of notifications:
AccessNotificationGranted
Notification is sent to open the access barrier, when the person in front of the access barrier is identified and is authorized to enter.
AccessNotificationDenied
Notification is sent when person is not identified against any of the watchlists, therefore is unknown. Optionally, AccessNotificationDenied is also sent when a person is identified but doesn’t wear a face mask or when the filtering strategies are not fulfilled.
AccessNotificationBlocked
Notification informs about the presence of an unauthorized person identified against a blacklist or when the spoof try is detected (e.g. face printed on a paper).
A special PING type of gRPC message is sent every 5 seconds without any further data. If this message type is requested by the client application, it can be used as a keepalive signal to determine if the connection is healthy and optionally try to reconnect to access controller if no PING message was received for the period of time.
How to Enable
For the proper functioning of SmartFace Access Controller it is required that SmartFace Platform is successfully installed and configured.
Setup on Windows
SmartFace Access Controller can be registered as a Windows service. It is recommended to install it on the same machine as the SmartFace Platform.
To install Access Controller:
Download the ZIP file for your version
SmartFace_AccessController_v5_<Version-Number>.zipfrom the Customer portal. To know which version matches your SmartFace Platform, please visit the releases tableExtract the ZIP file. We recommend extracting the file to
C:\Program Files\Innovatrics\Access ControllerRun the
Register_AccessController_Service.batfile.This
.batfile will register Access Controller application as the SFAccessController Windows service and start this service.
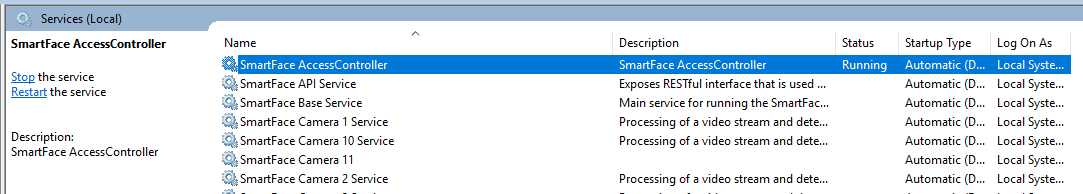
To verify the Access Controller is running:
If the Access Controller is sucessfully installed and is running you will see the information in the Windows Services with the status Running.
For more information about configuration and setup of the Access Controller, please visit the How to Setup page.
Setup on Docker
To enable Access Controller module using Docker on Linux add the lines below into your docker-compose.yml file. If you are using the “All-in-one” preset, it will be already there.
access-controller:
image: ${REGISTRY}sf-access-controller:${AC_VERSION}
container_name: SFAccessController
ports:
# we forward the configured ports to default SF ports
- 5050:${Hosting__Port}
restart: unless-stopped
environment:
- RabbitMq__HostName=${RabbitMQ__Hostname}
- RabbitMq__UserName=${RabbitMQ__Username}
- RabbitMq__Password=${RabbitMQ__Password}
- RabbitMq__Port=${RabbitMQ__Port}
- Kestrel__EndPoints__Http__Url=${Hosting__Host}:${Hosting__Port}
env_file: .env.sfac
To verify the Access Controller is running:
If the Access Controller is sucessfully installed and is running you will see the information whether it is up and for how long using the docker ps -a command. You can also search using the grep command such as in the situation below:
user@smartface-server:/srv/smartface$ docker ps -a | grep Access
1131fcd07d25 registry.gitlab.com/innovatrics/smartface/sf-access-controller:v5_1.9.1 "dotnet SmartFace.Ac…" 2 days ago Up 16 hours 0.0.0.0:5050->80/tcp, :::5050->80/tcp SFAccessController
For more information about configuration and setup of the Access Controller, please visit the How to Setup page.
Additional modalities
With additional modalities, such as the QR TOTP codes the Access Controller behaviour might differ to the behaviour for the Face Identification. In such a case, some of the filtering strategies are ommited as they are meaningful for these modalities.
QR TOTP
For the Time-based One Time Password encoded in QR code only the these filters are applies:
- Opening debounce
- Exclusive camera
- Blacklist configuration