NFC Chip Reading
DOT NFC is a mobile library enabling the reading of data from the RFID chip contained in the eMRTD with an NFC-enabled smartphone.
Electronic Machine Readable Travel Document - eMRTD
The eMRTD contains an NFC-readable RFID chip. This chip stores data from the travel document data page and the biometric data of the holder: the photograph and possibly other.
The data in the chip are digitally signed, and the country issuing an eMRTD maintains a dedicated public key infrastructure (PKI). The “Root” of this PKI is the Country Signing Certification Authority (CSCA). The document signer (DS) certificate, signed by the CSCA, proves the authenticity and integrity of the data on the chip and the link to the issuer.
Specifications and standards of eMRTD can be found in ICAO document series Doc 9303 Machine Readable Travel Documents.
DOT NFC Library
DOT NFC Library provides simple non-UI component - NFC Travel Document Reader (Android, iOS) which facilitates the NFC reading process. For Android DOT NFC library, there is also a UI component - UI NFC Travel Document Reader (Android).
The process contains the following steps:
- Access control
- Authentication of chip
- Reading and parsing data into structures
- Authentication of data
Access Control
In order to read the content of the eMRTD chip, Access Control has to be established. The Access Control mechanism ensures that data from the eMRTD chip is not read without the permission of the travel document holder.
There are two protocols for Access Control defined:
- BAC - Basic Access Control (this protocol is used if supported by the chip)
- PACE - Password Authenticated Connection Establishment (this protocol is used if BAC protocol fails or BAC is not supported by the chip)
Both Access Control protocols use an access password. There are two types of passwords:
- Password derived from the Machine Readable Zone (Document Number, Date of Birth and Date of Expiry).
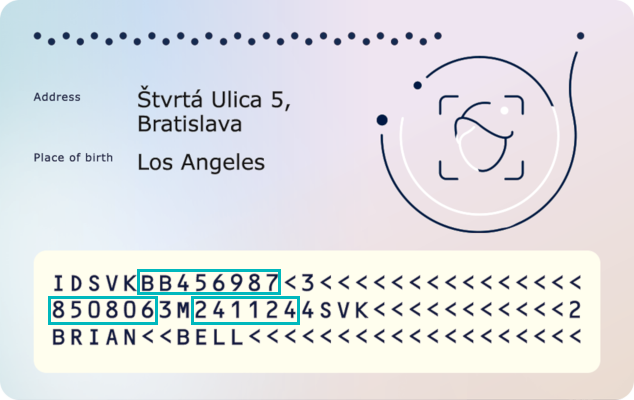
- Card Access Number (CAN) that is printed somewhere in the visual zone of the document.

Note: The password derived from the MRZ is suited for automatic processing, while the CAN is suited for manual typing.
After Access Control has been established, the chip will provide access to the available data groups.
Reading and parsing data
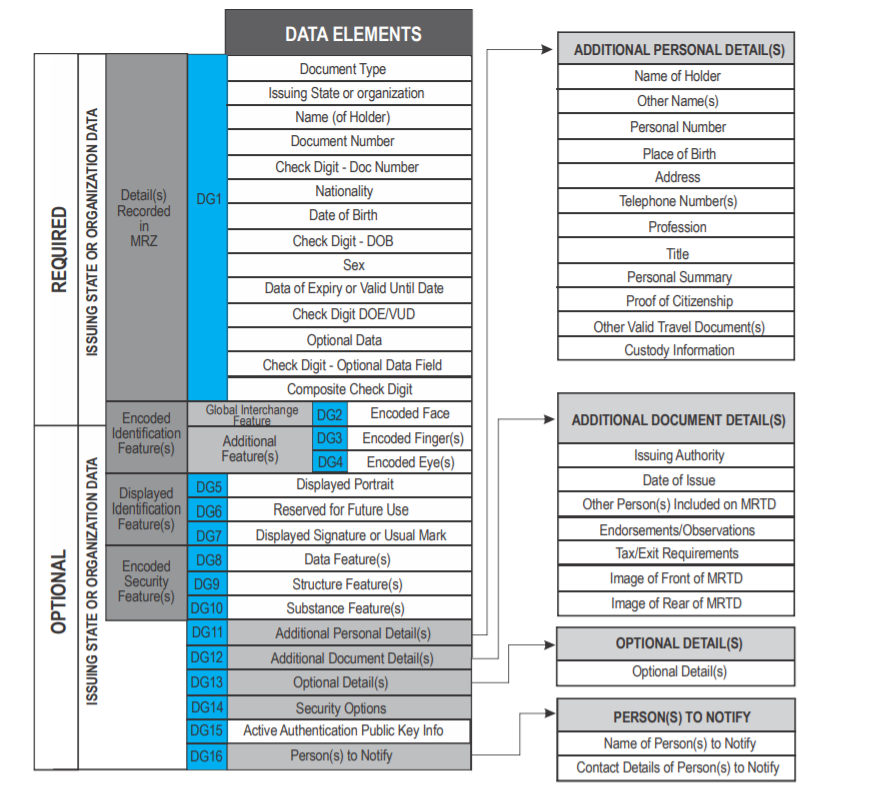
DOT NFC Library supports reading these Data Groups. Part of them are also parsed into structures.
| Data Group | Description | Structure |
|---|---|---|
| COM | Header and Data Group Presence Information (Mandatory) | |
| SOD | Document Security Object (Mandatory) | |
| DG1 | Machine Readable Zone Information (Mandatory) | MachineReadableZoneInformation |
| DG2 | Encoded Identification Features - Face (Mandatory) | EncodedIdentificationFeaturesFace |
| DG3 | Additional Identification Feature - Finger(s) (Optional) | |
| DG4 | Additional Identification Feature - Iris(es) (Optional) | |
| DG5 | Displayed Portrait (Optional) | |
| DG7 | Displayed Signature or Usual Mark (Optional) | DisplayedSignatureOrUsualMark |
| DG8 | Data Feature(s) (Optional) | |
| DG9 | Structure Feature(s) (Optional) | |
| DG10 | Substance Feature(s) (Optional) | |
| DG11 | Additional Personal Detail(s) (Optional) | AdditionalPersonalDetails |
| DG12 | Additional Document Detail(s) (Optional) | AdditionalDocumentDetails |
| DG13 | Optional Details(s) (Optional) | OptionalDetails |
| DG14 | Security Options (Conditional) | |
| DG15 | Active Authentication Public Key Info (Conditional) | |
| DG16 | Person(s) to Notify (Optional) |
The list of all possible data groups is below. Note that data groups DG3 and DG4 cannot be read without an additional certificate.