ID Document Authenticity
DOT contains a set of features that can help detect some of the most common signs of suspicious onboarding attempts.
To provide trusted digital onboarding, it is important not only to verify the user using facial biometrics and liveness, but also to evaluate the authenticity of the identity document.
Capabilities of the Hardware
Due to the limitations of smartphone cameras, it is currently not possible to reliably detect all fake or forged documents like with a dedicated document scanner. The only reliable method to prove document authenticity with a smartphone is the NFC reading of e-documents with a RFID chip.
However, there are certain features within the Digital Onboarding Toolkit (DOT) that may help to detect some signs of suspicious onboarding attempts. Human supervision is recommended to review suspicious documents.
Document Authenticity and Photo Capture Method
It is important that during the onboarding process there is no possibility for the user to upload a photo him/herself. It has to be strictly enforced that the user takes a photo of the document using only the DOT Document Auto Capture component. Being able to upload a photo of a document allows the user to make manipulations that cannot be detected.
Data Consistency
Biometric Validation
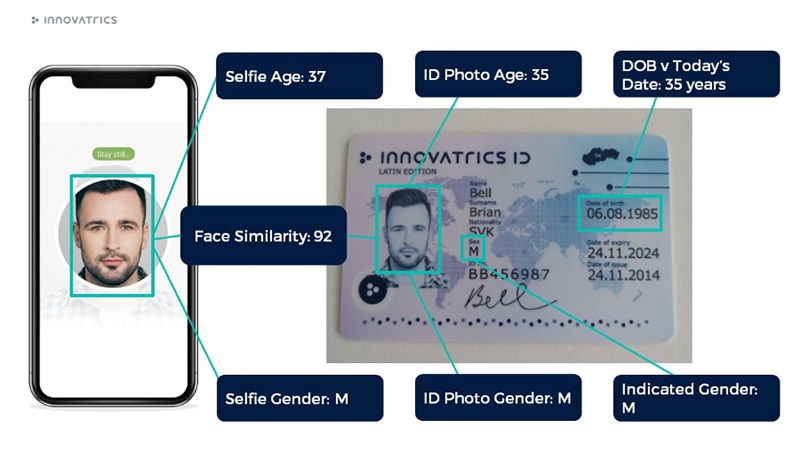
This is a core functionality of DOT. Our face algorithm provides an estimate of age and gender for the person in the selfie photo, as well as for the face portrait on the document. This can be validated against the date of birth and gender on the identity document. The cross check of selfie vs document photo confirms that the same person provided the selfie.
This validation result can be obtained in the SelfieInspection object of the response of the customers/{id}/inspect API call, and in the PortraitInspection object of the reponse of the customers/{id}/document/inspect API call.
If there is a significant difference between these and expected values, this can trigger an alert during the process, and such cases may be rejected or passed to manual review, based on the workflow configuration.
Document Data Cross-check
Some identity documents contain Machine Readable Zones (MRZ) and many have contactless RFID chips which can be accessed using NFC-capable smartphones. This provides two additional levels of document authenticity detection, as tampering with the MRZ field requires more advanced knowledge, and data from the RFID chip cannot be modified at all.
This validation result can be obtained in the VisualZoneInspection.TextConsistency object of the response of the customers/{id}/document/inspect API call.

RFID Chip Authentication
Besides the data cross-check, the document data read by NFC can be authenticated using Passive Authentication protocol. This is the only 100% reliable authentication method for ID documents. Read more in Passive Authentication
Visual Detection of Attacks
Older identity documents may not have RFID chips or an MRZ. DOT Document Server can detect some simple methods of document forging, including black and white photocopies. It can also detect photos of documents taken from a monitor or laptop screen.
Screen Attack Detection
The Digital Identity Service can detect if a photo of an ID document was taken from another screen, such as a laptop or monitor. This validation result can be obtained in the PageTamperingInspection.looksLikeScreenshot value of the response of the customers/{id}/document/inspect API call. This is returned per each document page separately.
Print Attack Detection
The detection method identifies as well, if the taken image of ID document is not a paper photocopy. This detection is enabled only for documents that are plastic by original. This validation result can be obtained in the PageTamperingInspection.looksLikePhotocopy of the same API call as above.